Can Law Enforcement use Cisco devices to spy on you? Yes they can!
Are Law Enforcement Agencies using your equipment to spy on you or others without you even knowing? Possibly!
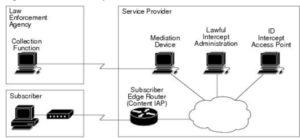
Lawful intercept is a process that enables a Law Enforcement Agency (LEA) to perform electronic surveillance on an individual (a target) as authorized by a judicial or administrative order. Congress requires that service providers (SPs) and Internet service providers (ISPs) implement their networks to explicitly support authorized electronic surveillance.
Because this: The service provider then intercepts the target’s traffic as it passes through the Catalyst 6500 series switch, and sends a copy of the intercepted traffic to the LEA without the target’s knowledge
See, you aren’t just being paranoid!
Get out your #TinFoilHat before you read on!
…and the winners are:
The surveillance is performed through the use of wiretaps on traditional telecommunications and Internet services in voice, data, and multiservice networks. The LEA delivers a request for a wiretap to the target’s service provider, who is responsible for intercepting data communication to and from the individual. The service provider uses the target’s IP address to determine which of its edge Catalyst 6500 series switchs handles the target’s traffic (data communication).
The service provider then intercepts the target’s traffic as it passes through the Catalyst 6500 series switch, and sends a copy of the intercepted traffic to the LEA without the target’s knowledge
Lawful intercept provides:
- Allows multiple LEAs to run a lawful intercept on the same target without each other’s knowledge.
- Does not affect subscriber services on the Catalyst 6500 series switch.
- Supports wiretaps in both the input and output direction.
- Supports wiretaps of Layer 1 and Layer 3 traffic. Layer 2 traffic is supported as IP traffic over VLANs.
- Supports wiretaps of individual subscribers that share a single physical interface.
- Cannot be detected by the target. Neither the network administrator nor the calling parties is aware that packets are being copied or that the call is being tapped.
- Uses Simple Network Management Protocol Version 3 (SNMPv3) and security features such as the View-based Access Control Model (SNMP-VACM-MIB) and User-based Security Model (SNMP-USM-MIB) to restrict access to lawful intercept information and components.
- Hides information about lawful intercepts from all but the most privileged users. An administrator must set up access rights to enable privileged users to access lawful intercept information.
- Provides two secure interfaces for performing an intercept: one for setting up the wiretap and one for sending the intercepted traffic to the LEA.
..While supplies last!
A mediation device (supplied by a third-party vendor) handles most of the processing for the lawful intercept.
The mediation device:
- Provides the interface used to set up and provision the lawful intercept.
- Generates requests to other network devices to set up and run the lawful intercept
- Converts the intercepted traffic into the format required by the LEA (which can vary from country to country) and sends a copy of the intercepted traffic to the LEA without the target’s knowledge.
Nice, huh?