Cisco’s really BIG – albeit quiet changes – in Firepower/FTD 6.3 code…
There are a couple new important changes in Firepower 6.3 code that fixed issues for a lot of my customers and all of my students. I had always known the work arounds for these issues, but by the time a customer either came to class or contacted me, they were frustrated beyond all belief. I am sure you know exactly the feeling I’m talking about if you’ve been using Cisco Firepower for the last 1-4 years…
FTD Platform Policy:
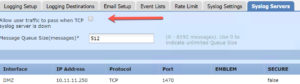
First, there was a major issue with the FTD Platform settings that Cisco never admitted to. Starting at 6.1 code, I refused to configure a platform setting on the FTD devices at my customer location. However, when 6.2.3 code came out, there were enough changes that made the platform settings mostly work as well as some needed lina syslogging, but again, no documentation regarding this from Cisco. This caused many a headache to my customers as their FTD boxes could just become a brick, and the FMC would show no activity at all since the issues for the platform were found in the Ingress Lina area; an area that sends no data to the FMC.
Based on my past experiences with ASA’s, I knew that configuring a Syslog using TCP could cause an issue if the syslog server went down, so I had some idea where to look as there was a work around with the ASA’s, and actually there was one as well with the FTD devices – just not documented, and this workaround setting was OFF BY DEFAULT so many of my customers unwittingly brought their FTD boxes to their knees if their syslog server lost connection to the FTD box.
However unlikely that you may feel this scenario would or could be, it certainly did occur to many customers and the results were disastrous. You could ping, etc the FTD devices but they passed NO PACKETS, and the FMC showed nothing, zero, zip.
Prior to 6.3 the shown check box was not enabled by default! Notice that it is now enabled and they even added the verbiage that they recommend it be enabled. Considering the issue that this can cause, this is understated.
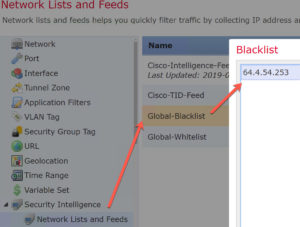
Objects: You no longer need to deploy after delisting a blacklisted host
In network analysis you can easily blacklist hosts, which is an awesome feature. However, it is easy to blacklist hosts, like your email server for example, by mistake.
To remove a host from the global blacklist, go to Objects>Network Lists and Feeds>Global-Blacklist, and then click on and remove the IP.
However, understand that when you right-click>blacklist an IP, the TCP session is dropped immediately. When you take an IP out of the blacklist you used to have to redeploy to push the new blacklist out, but with 6.3 the push is automatic. This is a HUGE change and crickets from Cisco! Just wow.
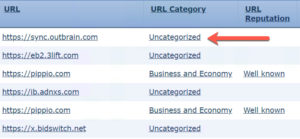
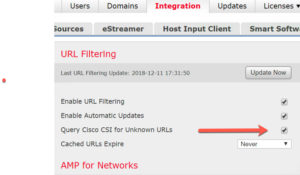
System>Integration>Query Cisco CSI for Unknown URLs:
Since Cisco released the first version of ASA with Firepower, this Query Cisco CSI setting under System>Integration was always off by default.
This means that when you filtered by URL category, it would come back as Uncategorized and allow the packets through instead of blocking a particular URL. By querying Cisco Security Intelligence for the URL category, it could then categorize the URL and immediately start blocking the packets.
When I went to enable this in System>Integration after installing 6.3 code and in order for my ACP with URL filtering rules to start blocking, the check box was already enabled! That is an absolutely huge, but quiet change that was sorely needed.
I could never figured out why it was disabled by default in the first place.
These three, but important changes really help out administration. Cisco never mentioned these changes, but we’ll take them. I am sure I’ll be adding a couple more shortly as I find them too…
Lastly, here is a minor change:
In the System>Configuration there is a new settings:
This is a Global User Configuration settings affect all users on the Firepower Management Center.
Why this isn’t under System>Users as a new tab is a good question, but from here you can set some global settings for all users, which was a needed feature for years.
Cheers!

It looks like Cisco has posted a new install file for 6.3.0, 6.3.0-84, replacing 6.3.0-83 and they have announced a few bugs that also affect 6.3.0.
oh wow..I’d love to say I’m shocked! :)
Thanks for the update Sally! Merry Christmas!